~Shrishti Sharma
What does your SMS inbox look like? The usual flurry of texts, appointment reminders, discount codes for your favorite stores, utility bills, travel updates, and more. Amidst this, there is one message that stands out: a seemingly official notification from your bank, might prompt you to confirm recent transactions, but in actuality it hasn’t come from your bank.
Now, that is what we call a smishing text message.
Smishing implies phishing attacks that utilise SMS as their medium, here attackers pose as legitimate organisations and trick people into giving away confidential and sensitive information, thereby incurring financial losses, identity theft, and more.
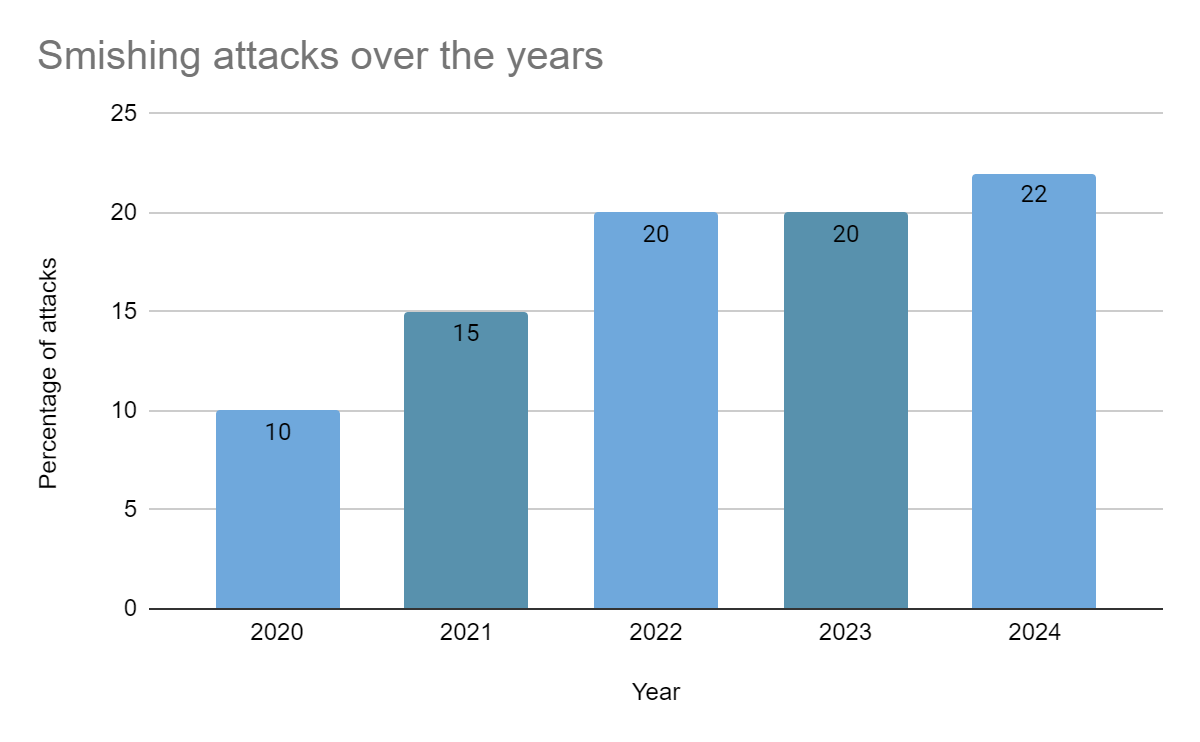
Speaking with ETBFSI, Ashish Sharma, Partner – Risk Advisory Services, Deloitte mentions that an average of 350,000 smishing attacks take place every day, and that figure is expected to rise.
Extrapolating the data on smishing attacks, Abhishek Biswal, Head for Digital Products, Airtel Business tells us that banking-related scams surged over 2X in H1FY23 from 2022, as per RBI data. As many as 14,483 frauds involving an amount of ₹2,642 crore were reported in the first half of FY 23, as compared to 5,396 cases (₹17,685 crore) in the same period a year ago; 52% of the scam messages are banking related scams.
What do Smishing attacks look like?
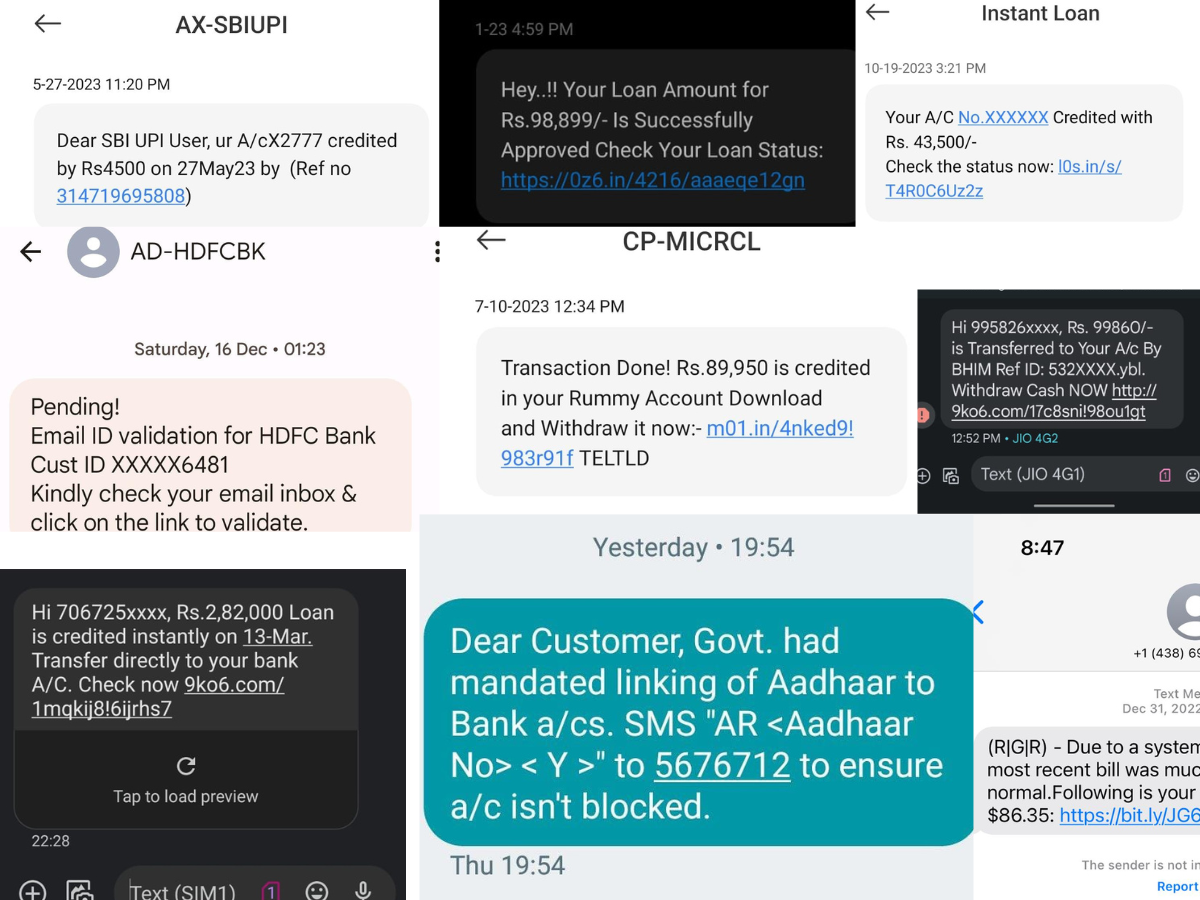
Impersonating the legitimate organisations, smishing messages can come in the form of fraudulent transaction confirmation, account lockdown alert, ATM card renewal, loan approval offers, insurance policy renewal, investment opportunities, salary/payroll updates, loan repayment assistance, and the list remains inexhaustible.
But Why a number as high as 3,50,000 per day?
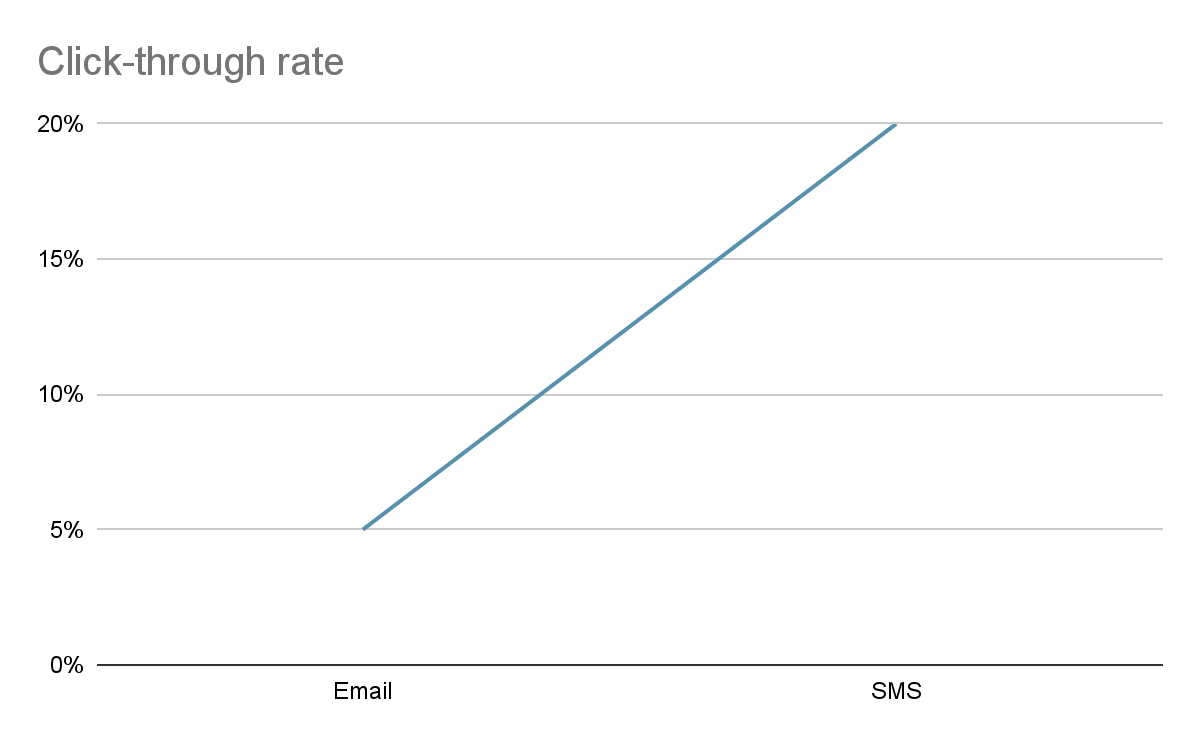
Ashish Sharma of Deloitte refers to a study from sinch, and explains, “SMS click-through rates hover around 20 per cent, compared to email’s click-through rates of 3-5 per cent. SMS response rates are as high as 45 per cent, therefore, recipients are more likely to engage with an SMS than an email, which has a 6 per cent average response rate.”
“With the widespread adoption of mobile devices for financial transactions, attackers have shifted focus towards targeting mobile users through smishing. This shift is driven by the prevalence of smartphones and the convenience they offer for banking activities,” said Shrikrishna Dikshit, Partner- Cyber Security, Nangia & Co LLP.
Also, individuals that do not own smartphones can also be preyed via text messages asking them to share confidential information, and hence adds to the vulnerability of a greater population.
“100% of new bank account openings in rural India are being done digitally. As more customers switch to digital banking, more customers are increasingly becoming susceptible to scams,” noted Abhishek Biswal, Head for Digital Products, Airtel Business.
“Automating the send-out times of smishing messages to coincide with times when recipients are most likely to be vulnerable, such as during peak shopping seasons or after a major data breach announcement,” said Khushbu Jain, Advocate, Supreme Court.
Tactics employed by Smishermen
“Attackers may also gather personal information from publicly available sources such as social media profiles, online directories, and public records. Information can also be obtained by attackers for a modest sum from various sources which have acquired customer data for legitimate purposes but are selling that data for a fee,” remarked Shrikrishna Dikshit, Partner- Cyber Security, Nangia & Co LLP.
And sometimes Phishing precedes Smishing
“Phishing attacks via email or other online channels may precede smishing attempts. In phishing attacks, individuals are tricked into providing personal information through fraudulent emails or websites that impersonate legitimate entities,” added Shrikrishna Dikshit of Nangia & Co LLP.
How do smishing attacks compare between different demographics?
Digital literacy is the governing factor while we try to analyse which segment of population is more prone to fall prey to a smishing attack.
“According to Google, Millennials and Gen-Z internet users (18-40 year olds) are most likely to fall victim to smishing attacks 23 per cent compared to 19 per cent of Generation X internet users (41-55 year olds). Users with supposedly high-income levels are 50% more likely to be targeted by smishing attacks,” noted Dikshit.
Enforcement challenges of smishing attacks
“The cross-border nature of smishing attacks complicates regulatory and enforcement efforts, as attackers can operate from different jurisdictions and evade detection more effectively,” commented Khushbu Jain, Advocate, Supreme Court.
Not just this, there are challenges at the systemic level too.
“While large financial institutions may have the resources to comply with stringent regulations, smaller entities might struggle to implement recommended or mandated security measures fully,” said Ashish Sharma of Deloitte.
Legal hurdles in prosecuting smishing offenders
“Prosecuting smishing attackers often run into legal problems because the crimes can cross international borders, the attackers hide behind the anonymity of digital communication and it’s hard to figure out who’s behind the attacks,” Khushbu Jain, Advocate, Supreme Court.
She also adds that the proposed Digital India Act 2023, aims to tackle new technologies and risks and aims to be flexible and in line with evolving market trends, technological disruptions, developments in international law, and global standards for quality service and product delivery.
How should the BFSI institutions mitigate smishing?
- Implementing multi-factor authentication (MFA) to enhance security and verify user identity, reducing the risk of compromised accounts.
- Conducting extensive security awareness campaigns to educate employees and customers about smishing tactics and how to recognise and report suspicious messages.
- Deploying advanced threat detection solutions, including email and SMS filtering, anomaly detection, and behavior analysis, to detect and block smishing attempts in real-time.
- Collaborating with telecommunications providers and industry partners to share threat intelligence and coordinate response efforts.
- Ensuring compliance with regulatory guidelines issued by bodies such as RBI and NPCI to strengthen cybersecurity measures and protect customers from fraudulent activities.
- Monitoring and analysing SMS traffic patterns to detect anomalies and block suspicious messages before they reach users’ devices.
- Investing in anti-phishing and anti-spoofing technologies to identify and block fraudulent messages effectively.
- Promoting the use of official banking apps and websites to educate customers about the risks of smishing and encourage secure banking practices.
Return of Investment for BFSI Institutions
Dikshit explains that implementing advanced smishing detection and prevention technologies in BFSI organisations yields significant returns on investment across various fronts. By reducing fraudulent transactions, improving operational efficiency, enhancing customer trust and loyalty, and ensuring compliance with regulatory standards, these technologies offer tangible benefits. Through streamlined incident response processes, increased customer satisfaction, and effective regulatory adherence, BFSI institutions can safeguard their assets, reputation, and customer relationships.
AI that is harnessed for both offence and defence
“AI algorithms can sift through huge amounts of data to find who to target with smishing, making these attacks more personal and effective, can help automate the making and sending of smishing messages, as well as help them avoid security checks,” said Khushbu Jain, Advocate, Supreme Court of India.
Jain adds that AI allows for smishing attacks to be fine-tuned in real-time. By watching how people respond, attackers can change their tactics to improve their chances and avoid getting caught.
This is how Smishermen are utilising AI, and at the same BFSI institutions are also leveraging the technology to prevent such attacks.
“Entities in the BSFI sector are now focusing more on AI-driven solutions such as Natural language processes that can analyse the text of messages based on the language, phrases, and patterns commonly used by attackers and behavioral biometrics that involves analysing user behavior patterns, such as how they typically interact with banking apps or websites,” mentioned Ashish Sharma, Partner, Deloitte.
“AI/ML based solutions enable banks to proactively detect, prevent, and eliminate phishing, spam, and fraud through messaging. The artificial intelligence-powered solution also enables 100% message delivery of customer messages while also enabling multi-touch points as fallback options – SMS, voice & WhatsApp,” said Abhishek Biswal, Head for Digital Products, Airtel Business.